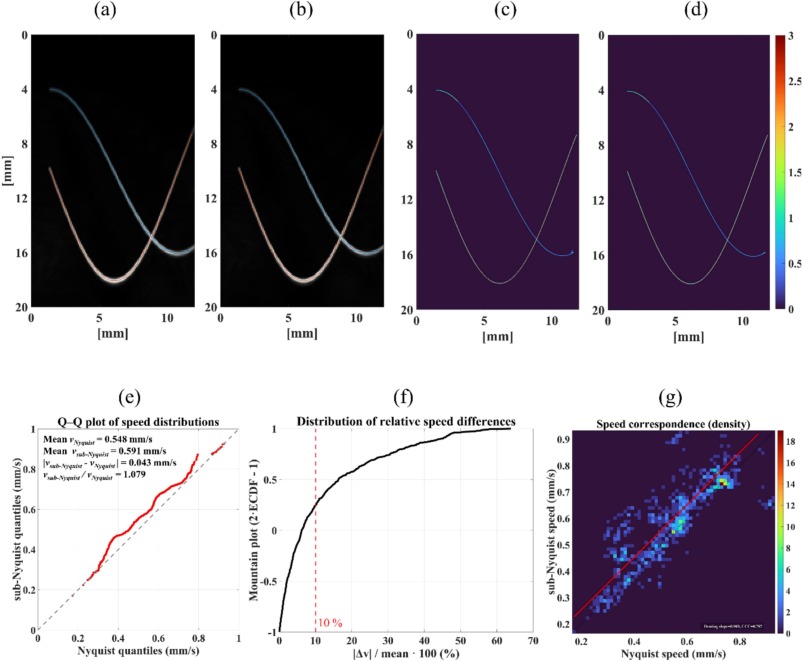
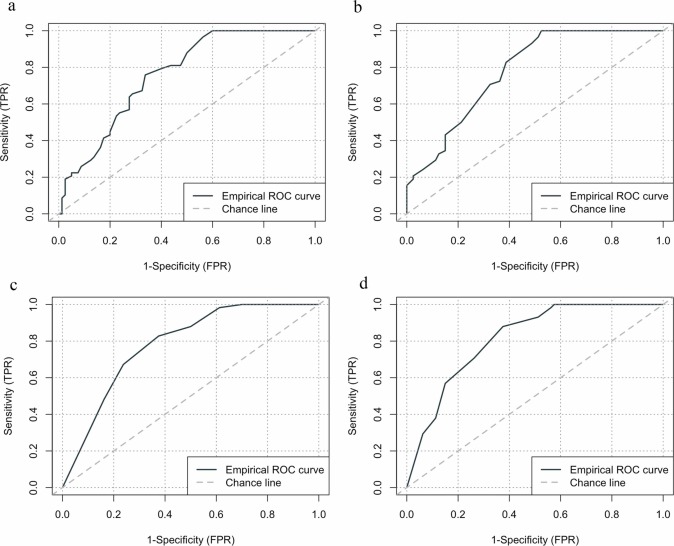
우리 연구팀이 참여한 COH-FIT 국제공동연구의 논문이 출판되었습니다.

Collaborative Outcomes Study on Health and Functioning During Infection Times (COH-FIT): Global and Risk-Group Stratified Course of Well-Being and Mental Health During the COVID-19 Pandemic in Adolescents. Solmi M, Thompson T, Cortese S, Estradé A, Agorastos A, Radua J, Dragioti E, Vancampfort D, Thygesen LC, Aschauer H, Schlögelhofer M, Aschauer E, Schneeberger AA, Huber CG, Hasler G, Conus P, Do Cuénod KQ, von Känel R, Arrondo G, Fusar-Poli P, Gorwood P, Llorca PM, Krebs MO, Scanferla E, Kishimoto T, Rabbani G, Skonieczna-Żydecka K, Brambilla P, Favaro A, Takamiya A, Zoccante L, Colizzi M, Bourgin J, Kamiński K, Moghadasin M, Seedat S, Matthews E, Wells J, Vassilopoulou E, Gadelha A, Su KP, Kwon JS, Kim M, Lee TY, Papsuev O, Manková D, Boscutti A, Gerunda C, Saccon D, Righi E, Monaco F, Croatto G, Cereda G, Demurtas J, Brondino N, Veronese N, Enrico P, Politi P, Ciappolino V, Pfennig A, Bechdolf A, Meyer-Lindenberg A, Kahl KG, Domschke K, Bauer M, Koutsouleris N, Winter S, Borgwardt S, Bitter I, Balazs J, Czobor P, Unoka Z, Mavridis D, Tsamakis K, Bozikas VP, Tunvirachaisakul C, Maes M, Rungnirundorn T, Supasitthumrong T, Haque A, Brunoni AR, Costardi CG, Schuch FB, Polanczyk G, Luiz JM, Fonseca L, Aparicio LV, Valvassori SS, Nordentoft M, Vendsborg P, Hoffmann SH, Sehli J, Sartorius N, Heuss S, Guinart D, Hamilton J, Kane J, Rubio J, Sand M, Koyanagi A, Solanes A, A… J Am Acad Child Adolesc Psychiatry. 2025 Apr;64(4):499-519. doi: 10.1016/j.jaac.2024.07.932.
https://linkinghub.elsevier.com/retrieve/pii/S0890-8567(24)02023-9